What is the Scrypt Mining Algorithm?

If you’ve spent even a little time diving into the world of cryptocurrency, chances are you’ve run across names like Litecoin and Dogecoin. They’re not just Bitcoin’s quirky cousins or second-string players in the crypto league — they actually use a completely different mining algorithm called Scrypt.
But here’s the twist: while most people have heard about Bitcoin’s famous SHA-256 algorithm, very few can actually explain what Scrypt is or why it even matters. If you’ve ever found yourself scratching your head at the mention of it, don’t worry — you’re not alone.
This guide breaks everything down in plain, no-nonsense English — where Scrypt came from, how it actually works, and why it’s such a game-changer in the cryptosphere. So, grab your metaphorical mining helmet — we’re about to dig deep into what makes Scrypt tick.
What is the Scrypt Algorithm?
At its simplest, Scrypt is what tech folks call a password-based key derivation function (KDF). Sounds technical, right? But here’s the gist: a KDF takes a secret (like a password or key) and transforms it into something far stronger — a long, secure cryptographic key.
Think of it like taking your easy-to-remember password and turning it into an ironclad secret code that no one can crack.
Key Characteristics of Scrypt:
Memory-Hard Design:
Unlike older algorithms such as PBKDF2, Scrypt demands not only heavy computation but also large chunks of memory. This combination makes it extra tough for attackers or specialized machines to brute-force.Built for Security (Not Mining):
Interestingly, Scrypt wasn’t born in the crypto mines — it was designed to protect sensitive data like encrypted files and online backups.Crypto’s Adopted Child:
Over time, its robust design made it a natural fit for cryptocurrencies like Litecoin (LTC) and Dogecoin (DOGE), both of which rely on it for mining operations.
How Does the Scrypt Algorithm Work?
Alright, let’s break it down into bite-sized steps. No technical jargon, just straight talk.
Start with a Password (or Block Header):
In mining, this “password” is the block header — the data miners are trying to hash.Mix It Up:
Scrypt passes the input through a pseudorandom function, creating a unique, unpredictable string.Memory-Heavy Workload:
This is where Scrypt flexes its muscles. It stores large amounts of data in RAM and constantly reads and writes from it. This back-and-forth dance makes it nearly impossible for ASICs to cheat the system.Generate the Key:
The final output is a derived cryptographic key — or, in mining terms, proof that the miner has done legitimate, memory-intensive work.
Advantages of Scrypt
Why should anyone care about Scrypt? Well, it’s got more than a few advantages worth bragging about:
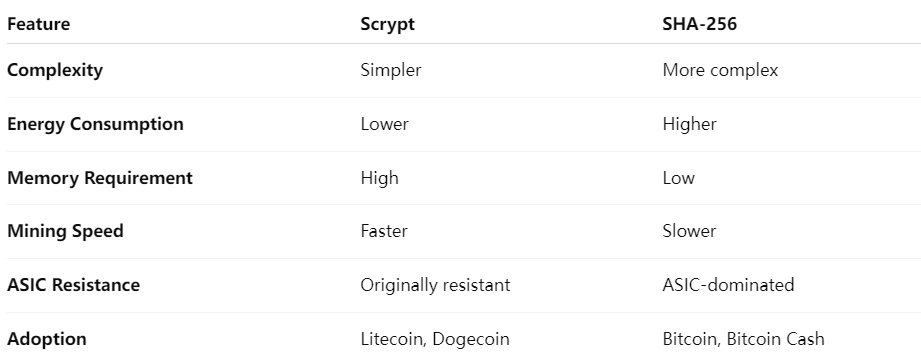
Less Complex: Easier to implement compared to SHA-256.
Energy Efficient: Uses less power overall, making it eco-friendlier than many other algorithms.
Faster Mining: Scrypt-based coins can be mined roughly four times faster than Bitcoin.
Lower Fees: Networks that use Scrypt often feature cheaper transaction fees.
Versatile Security: Perfect for not just crypto, but also password hashing and encrypting sensitive data.
Scrypt vs SHA-256: The Big Showdown
Let’s be honest — both algorithms are impressive in their own right.
SHA-256 is a powerhouse of raw security and remains the backbone of Bitcoin.
Scrypt, on the other hand, prioritizes accessibility and fairness. It made mining more inclusive by slowing down ASICs and encouraging participation from ordinary users.
Read More: What Are Crypto Mining Algorithms?

Popular Cryptocurrencies That Use Scrypt
If you’re into mining or investing, it’s good to know which digital coins are built around Scrypt. Here are some of the most well-known names in the space:
Litecoin (LTC):
Often called the “silver to Bitcoin’s gold,” Litecoin is the most famous Scrypt-based coin and played a major role in introducing the algorithm to blockchain technology.Dogecoin (DOGE):
What started as an internet joke quickly became a cultural icon. Behind the memes, though, Dogecoin relies on Scrypt for its mining operations.Feathercoin (FTC):
A smaller altcoin that quietly uses Scrypt under the hood, offering faster transactions and lower fees.Viacoin (VIA):
Another Scrypt-powered project focused on speed and scalability within the crypto ecosystem.
Frequently Asked Questions about Scrypt
Q1: What is the Scrypt algorithm and how does it work, in simple terms?
Scrypt is a cryptographic process that mixes intense computation with heavy memory usage to generate secure keys or verify crypto transactions. Its design helps prevent specialized machines from taking over the mining process.
Q2: Why is Scrypt called a “memory-hard” algorithm?
Because it requires computers to constantly store and access large chunks of data in RAM while processing — a method that slows down ASICs and makes brute-force attacks less efficient.
Q3: Which cryptocurrencies currently use Scrypt?
Some of the best-known Scrypt-based coins include Litecoin, Dogecoin, Feathercoin, and Viacoin.
Q4: Is Scrypt still ASIC-resistant today?
Not entirely. Modern ASICs can now mine Scrypt efficiently, though the algorithm’s design still demands more memory than SHA-256, keeping it relatively balanced.
Q5: Can Scrypt be used outside the crypto world?
Definitely. It’s used in password hashing, file encryption, and data backup systems — anywhere security and privacy matter.
Conclusion
So, what’s the takeaway here? When someone asks, “What is the Scrypt algorithm and how does it work?” — you can tell them it’s a memory-hard cryptographic function that started out protecting passwords and files, and later found fame powering cryptocurrencies like Litecoin and Dogecoin.

